See and Manage Yourthalor Account Activity History: Take Full Control of Your Digital Footprint
See and Manage Yourthalor Account Activity History: Take Full Control of Your Digital Footprint
Your Google Account activity history is more than just a log of recent actions — it’s a comprehensive digital diary of every search, sign-in, file access, and app interaction. Managing this history empowers users to safeguard privacy, detect security threats, and maintain transparency over their online presence. With growing concerns over data exposure, understanding how to view and refine your account activity has never been more critical.
Whether you’re protecting personal information from unauthorized use or auditing past behavior for compliance, accessing and curating your activity history offers tangible control over your digital life.
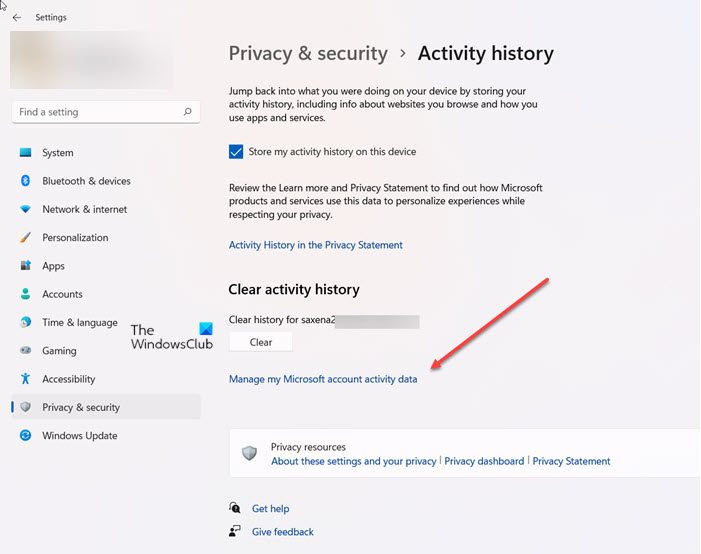
Accessing your full activity timeline begins with a single, deliberate step within your Google account settings. Navigate to Activity, where a detailed chronological record unfolds.
This dashboard displays individual events such as sign-ins from new devices, email sends, keyword searches, and app usage — each flagged with timestamps and location data where enabled. For enhanced clarity, events are grouped chronologically, with recent activities appearing first, though filtering by date range allows users to dive into specific periods without distraction. This structured view transforms the sometimes overwhelming flood of digital actions into an organized, actionable timeline.
Decoding the Significance of YourActivity Log
Every timestamped entry in your voir and manage your美国心理学会volution history serves a purpose beyond mere annotation.Timestamped records reveal patterns: frequent logins from unfamiliar IP addresses may signal account compromise, while recurring searches could indicate professional intent or ongoing research. Location intelligence, when enabled, adds context—flagging unusual access from abroad during regular work hours. Critical events such as password resets, device additions, and data export requests are clearly marked, enabling swift identification of both benign and suspicious behavior.
This level of visibility extends beyond personal oversight. Organizations relying on员工 account access use activity logs for audit compliance, data governance, and cybersecurity monitoring. For individuals, the ability to review and anonymize past recordings—deleting or archiving sensitive data—ensures alignment with privacy best practices.
Analyzing the history helps uncover inefficient tool use, unnecessary permissions, or recurring actions that might otherwise go unnoticed, fostering better digital hygiene.
Step-by-Step: How to Access Your Activity History
To begin managing your account activity, follow these clear, actionable steps:- Log in to your shove account using your correct email and password.
- Once authenticated, locate the "Security" or "Privacy & security" section—typically accessible via the top menu or profile icon.
- Click “Activity history” to instantly load your browsing and interaction log.
- Use the time-range filter (e.g., last 7 days, 30 days, or Custom range) to narrow focus.
- Each event displays key metadata: timestamp, action type (search, login, file download), device details, and location.
- Interact with filters such as “Security events” to isolate login attempts, device changes, or suspicious sign-ins for in-depth analysis.
Advanced users can enhance this review with copy-paste functionality or download options, enabling seamless archiving for offline reference.
The interface adapts to both mobile and desktop, ensuring accessibility across devices—critical for users managing accounts in varied environments.
Strategies for Proactive Account Management
Merely viewing activity is only the first phase; effective management requires intentionality. Experts recommend routine checks—weekly or monthly—to maintain vigilance. Here are proven tactics:- Delete irrelevant entries: Remove temporary test data, cached IP logs, or old authentication attempts no longer useful.
- Spot and respond to anomalies: Immediately review logins from unknown locations or unusual devices—trigger multi-factor authentication prompts and reset passwords if needed.
- Limit third-party data sharing: Audit connected apps and services; revoke access to unused tools that persist in activity logs.
- Enable alerts: Set up notifications for sign-ins on unrecognized devices or abrupt location shifts—this proactive layer catches threats faster than manual checks.

Related Post

Cricket World Cup 2027: Dates, Teams, And What To Expect

Dog Breeds Closest To Wolves: Unveiling the Wild Within

Vikram Actor Height: What Science and Stardom Reveal About the Talented Star’s Physical Presence on Screen
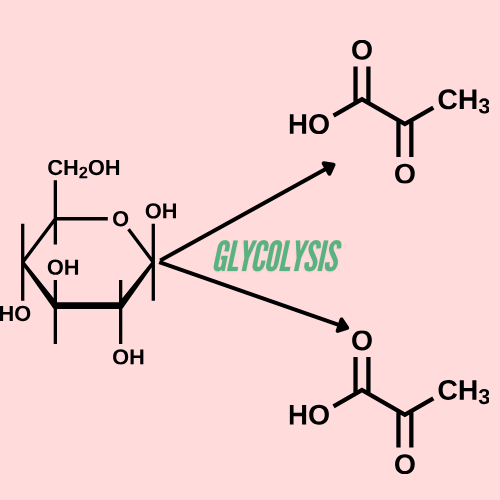
Reactant of Glycolysis: The Crucial First Step in Cellular Energy Production

